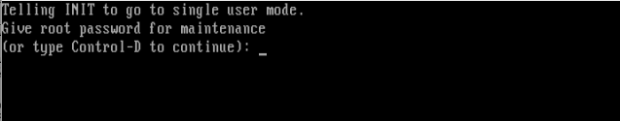
Here we are covering on topic “Hacking into a Linux system”. Passwords are one of the main mechanism to login to a system, in case of a Linux system it’s not different. If you have access to the root password you have access to the entire system. Here i’m covering a small tutorial for how to hacking into a Linux machine.
Hacking from single user mode
During startup of the system press any key to interrupt the Grub Loader
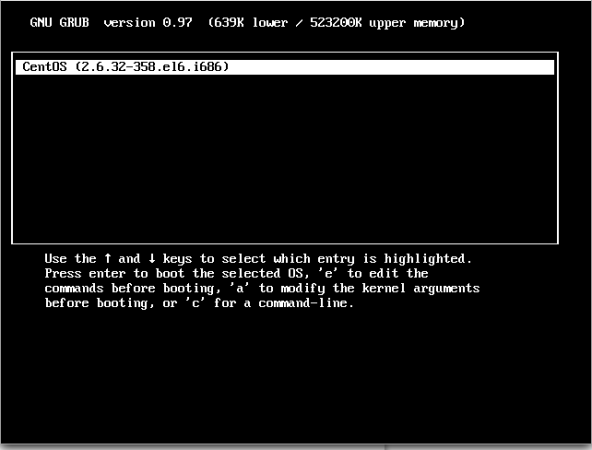
Press ‘e’ to edit, and go to the line starting with kernel (2nd line in almost all cases)
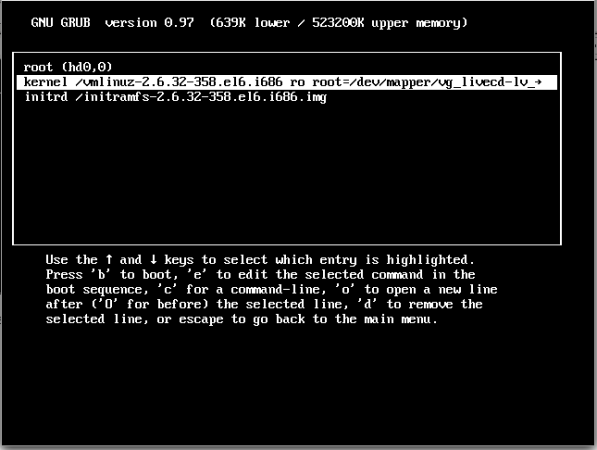
Press ‘e’ to edit and add ‘1’ at the end of the line after space after the last word, you can use ‘s’ also instead of ‘1’.
Adding this entry will force the system to start in “Single User mode” and skip the default run level. Press ‘enter’ to complete editing and press ‘b’ to continue the boot process.
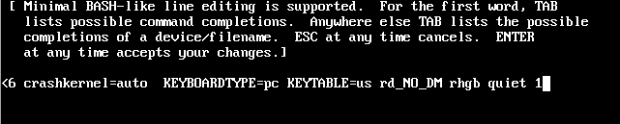
Now you are logged into a single user mode.
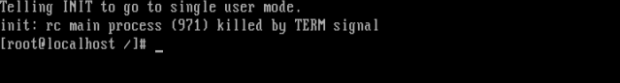
We can issue the ‘passwd’ command to change the root user password.
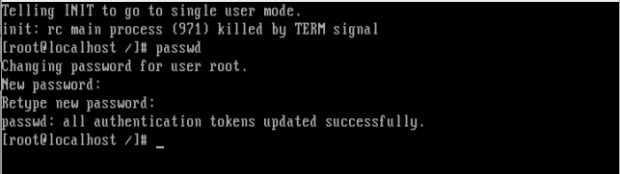
Note: if SELinux is enabled, the above ‘passwd’ command may return blank. If it is returned blank it means SELinux is enabled and in enforcing mode, hence we need to disable SELinux
For disabling SELinux, type ‘setenforce 0’ @ the terminal prompt.
#setenforce 0
FIX: So now we know how to login to a Linux system by hacking root password using single user mode. But what if we want to fix this vulnerability?
For password protecting single user mode, open file "/etc/rc1.d/S99single" and add the following line
exec sbin/sulogin
This should be added before
exec init -t1 s
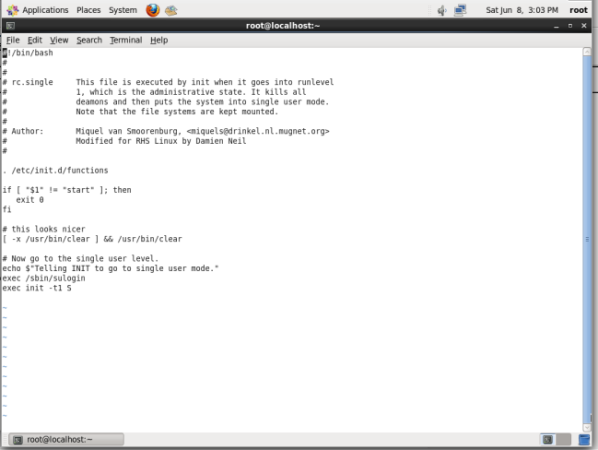
Once the changes are made reboot to Single use mode and have a check, it will be asking for a password to login to Single user mode.